Rethinking Data Security: The Shift from DLP to DDR
The Evolving Landscape of Data Security
Sensitive information is increasingly shared across various endpoints and environments, heightening its exposure to a broader range of risks.
Traditional security measures like database protection, Data Loss Prevention (DLP) tools, and network security solutions are designed to secure data perimeters and monitor outbound data. But as business environments become more dynamic, data movement and access have become more complex. Internal threats—such as employee errors, unauthorized access after departure, and insider threats—are more frequent and harder to detect.
What the Industry Needs in 2025
In 2025, businesses must gain complete visibility into how data flows, where it moves, and who is handling it.
This visibility is crucial for both compliance and risk detection. Organizations need to track data usage across accounts, applications, and endpoints while monitoring both structured and unstructured data throughout its entire lifecycle. Only with this level of oversight can companies protect their data, ensuring integrity and compliance in an ever-changing digital landscape.
Limitations of Traditional DLP
Traditional Data Loss Prevention (DLP) solutions rely on static rules and pattern-matching engines to monitor data, mainly when it's in motion, especially during outbound transfers.
- Inefficiency and High False Alerts: DLP's rigid rule sets often disrupt workflows without considering context, leading to false positives. Additionally, it struggles to protect unstructured content, such as design files, handwritten documents, or encrypted and compressed data.
- Invisibility into Insider Threats: DLP can't correlate data actions with specific users or endpoints, making it difficult to track leaks and identify the responsible parties.
- Delayed and Reactive Risk Detection: DLP only detects risks when data leaves the organization, often missing the earlier stages when sensitive data is created or modified internally. If data doesn't move outbound, DLP fails to identify potential exposure, leaving critical security gaps.
What is the Difference Between DLP and DDR
Data Loss Prevention (DLP) is designed to stop sensitive information flowing where it shouldn’t. It works by inspecting content across data‑in‑use (like typing or copying), data‑in‑motion (such as email or file transfers), and data‑at‑rest (stored files). Policies built on pattern matching, data classification, and predefined rules determine what gets blocked, encrypted, or flagged. The goal is to actively prevent leakage before it happens. It’s widely used for compliance (e.g. GDPR, HIPAA), but can be prone to generating false positives and often requires extensive tuning and maintenance
In contrast, Data Detection and Response (DDR) focuses on detecting suspicious activity involving sensitive data and responding in real‑time. Instead of scanning static content periodically, DDR continuously monitors data behavior across cloud, endpoints, and collaboration tools—constructing a live lineage of data flows. When unusual or risky behavior occurs (e.g. an employee mass downloads a customer list), DDR tools trigger alerts and automated actions such as blocking transfers, redacting content, or initiating workflows
One key advantage of DDR is its context‑aware and behavior‑based analytics. Rather than relying solely on strict rule‑based prevention, DDR understands user and data behavior over time, reducing false positives and enabling more targeted response actions. Many DDR solutions are agentless, making them easier to deploy—especially across cloud and hybrid environments where installing agents isn’t feasible.
How DDR Addresses These Gaps
Data Detection and Response (DDR) offers a smarter, context-aware solution that continuously monitors data from creation through its entire lifecycle, addressing the shortcomings of DLP.
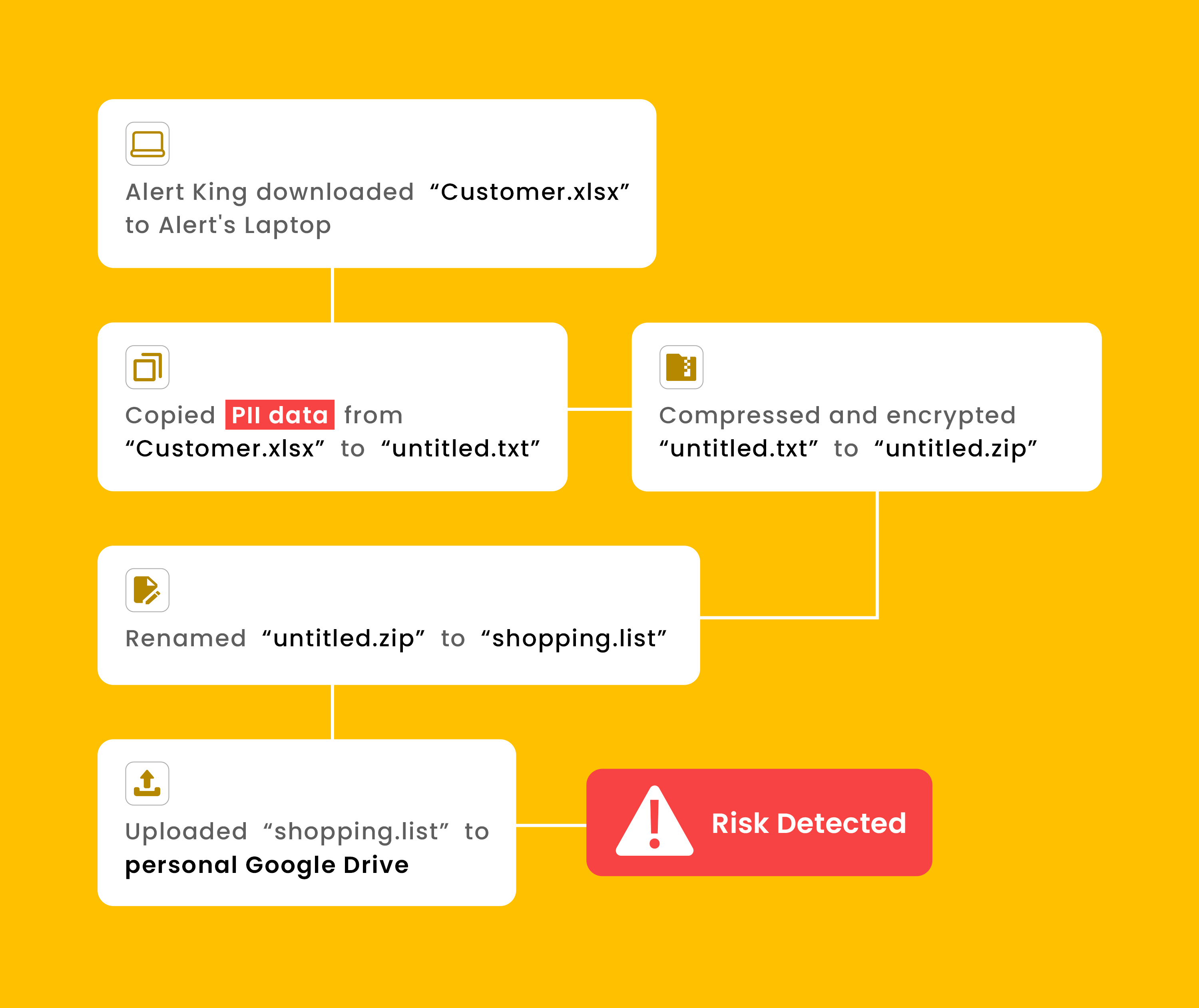
- Context-Aware Classification and Reduced False Positives: Powered by AI, DDR classifies data based on its real-world usage context rather than rigid pattern matching. This significantly reduces false positives while enhancing protection, especially for unstructured content like design documents, handwritten files, and encrypted data that DLP often overlooks.
- User and Endpoint Correlation to Expose Insider Risks: DDR integrates User and Entity Behavior Analytics (UEBA) and Information Rights Management (IRM) to map data activities to specific users and endpoints. This provides clear visibility into who is accessing or misusing sensitive information, making it easier to trace and address insider threats.
- Proactive Risk Detection and Full Lifecycle Monitoring: DDR begins monitoring sensitive data as soon as it's created or modified—not just when it leaves the organization. By tracking data across its entire lifecycle, DDR enables early detection, preventing risks before they escalate. This proactive approach fills the gaps DLP misses, identifying both internal and external threats.
The Future of Data Security: Control Over Data, Not Just Perimeter Defense
The future of data security lies in both data and user centric control, not just blocking data leaks, but understanding and managing how it flows within and outside the organization. The shift from DLP to DDR represents a critical step forward in data protection, enabling organizations to tackle the complex challenges of today’s data landscape with confidence. Contact us for comprehensive data security solutions.
