Why are traditional DLP products not efficient enough? What is DDR?
DDR will completely change the concept of traditional data protection, just as the changes brought by EDR to endpoint safety.
01 The Evolution from Antivirus Software to EDR
With the changing threat landscape, endpoint security has evolved from static to dynamic, and from point-based to global defense. Here's a look at this progression:
- First Generation: AV / NGAV
1980s ~ 2000s Static Signature Matching
- Focused on threats such as computer viruses and Trojan horses.
- Used static signature matching to identify and block malware by extracting and matching binary file characteristics.
- Second Generation: EPP 2000s ~ 2010s Combining Static Signatures with Dynamic Behavior Focused on emerging threats like rootkits, malicious plug-ins, traffic trojans, and password-stealing software.Introduced digital signature-based certification systems, combining static signatures with dynamic behavior analysis. Introduced cloud security and heuristic scanning to enhance local sample databases and improve detection algorithms.
- Third Generation: EDR
2010s ~ Present Threat Lifecycle Awareness and Protection
- Focused on advanced persistent threats and more sophisticated, ongoing threats.
- Shifted from passive, point-based defense to active, global threat detection and response.
- Introduced methods like machine learning and data analytics to quantify attack-defense dynamics and provide real-time incident response capabilities.
02 The Single Point of Failure in Traditional DLP
Just like the evolution of endpoint security, traditional DLP products mainly rely on rule sets and matching engines to perform static scans of files. Data is inspected at the moment it is sent, much like a vehicle passing through a high-speed checkpoint: vehicles that store prohibited items (sensitive data) in their trunks are usually flagged, while more sophisticated evasion tactics, such as hiding prohibited items under a disassembled seat, often go unnoticed.
A simple example
For any outgoing file, if we XOR the file with a string such as 0x7765206c697374656e2c77652068756e74, no traditional DLP product’s rules or models would be able to identify what the file originally was. It would only be recognized as a binary file.
After sending it out, the recipient can simply XOR the received file with 0x7765206c697374656e2c77652068756e74 again, and they will recover the original file.
Traditional DLP vendors focus more on conventional and data-specific content inspection methods, which can lead to incident fatigue and a siloed view of data movement.
— Market Guide for Data Loss Prevention
Gartner, 2022
03 How DDR Solves the Single Point of Failure
DDR addresses the issue of single point failures by monitoring the file from the moment it is created. For instance, if you download a sensitive file, such as "secret.xlsx", from an internal system, and then copy a part of it into a new document "good.docx", encrypt and compress it into "a.zip", and send it via an encrypted channel (e.g., Signal or other encrypted communication tools), traditional endpoint DLP would not be able to detect the contents of "a.zip". Network DLP, on the other hand, wouldn't be able to see the file at all due to encryption. Only by monitoring the file from its source and tracking its changes at each stage can we recognize that it contains sensitive data and stop it from being sent out.
The core idea behind DDR is a shift from simply checking the content of a file to combining the file’s "origin and destination" information for a more comprehensive judgment. This allows for simpler content recognition rules while also improving the accuracy of identifying sensitive files that may be hard to define through traditional rule-based methods.
For example, in an e-commerce context, sensitive information often involves promotional images for a big sale
Traditional Approach: Using OCR to scan image content and apply rules to determine if the content is sensitive. However, due to artistic fonts and design elements, recognition often fails. Moreover, even if the phrase “We will give the first 300 customers a 50% discount” is detected, it is hard to define it as "sensitive" based on content alone. However, if this image is leaked to a competitor, they could use this information to offer a much more targeted campaign, such as “We will give the first 300 customers a 70% discount.”
DDR Approach: We could define that any file generated by a designer’s software (e.g., Photoshop or other graphic design tools) is considered sensitive. By tracking these files through all transformations, DDR ensures better protection against the leak of sensitive promotional data.
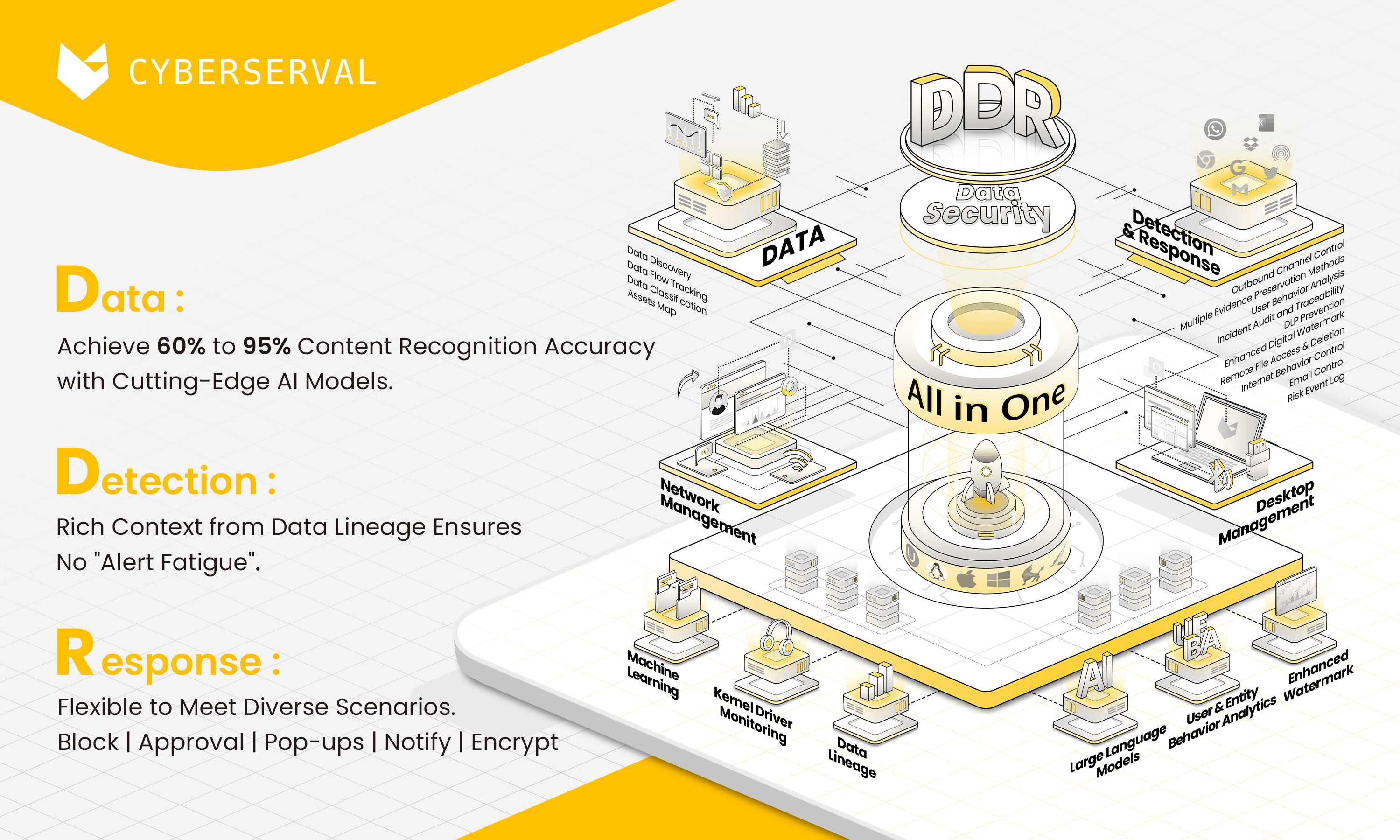
We believe that DDR’s key technology is "full lifecycle data monitoring", or as known as Data Lineage. This involves recording the creation, modification, and movement of any data, no matter where it occurs—whether on endpoints, networks, or in the public cloud. This continuous monitoring enables better data security, and it is the core difference between DDR and traditional DLP solutions.
