Why DDR is a Better Data Security Solution than DLP
Data security is evolving rapidly, and traditional solutions like DLP are no longer enough.
As cyber threats grow more sophisticated and regulations tighten worldwide, businesses face increasing pressure to strengthen their defenses. High-profile breaches have exposed the weaknesses of outdated, rule-based systems, demonstrating that static protection is no longer effective. To stay ahead of emerging risks, organizations need smarter, real-time solutions—DLP alone can no longer keep up.
What is Data Loss Prevention (DLP)?
Data Loss Prevention (DLP) is a security strategy designed to prevent unauthorized access, sharing, or leakage of sensitive data. Traditional DLP solutions rely on static rules, keyword matching, and predefined policies to monitor data movement across endpoints, networks, and cloud environments.
Organizations use DLP to comply with the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI-DSS), and other regulations, ensuring that customer records, intellectual property, and financial data remain protected. However, as cyber threats become more sophisticated, DLP’s effectiveness has declined.
"DLP technology is mature, but today, organizations look for comprehensive solutions that go beyond traditional DLP measures. Security and risk management leaders should focus on risk-based adaptive data protection techniques to strengthen the data security of their organization." — Gartner, Market Guide for Data Loss Prevention.
What are the disadvantages of DLP?
For years, DLP has been a cornerstone of data security. However, its reliance on static detection methods presents serious challenges:
- Rigid, Rule-Based Detection – DLP relies on predefined rules and keyword matching, making it easy to bypass with simple techniques like encoding, encryption, or slight modifications to sensitive content.
- Frequent False Positives & Missed Threats – Many DLP systems overwhelm security teams with false alarms while also failing to detect more sophisticated attacks.
- Lack of Data Lifecycle Visibility – Traditional DLP only scans data at specific checkpoints (e.g., email attachments, USB transfers, or network uploads), but doesn’t track how data evolves over time.
- Weakness Against Insider Threats – Malicious insiders can bypass static DLP rules by altering data, using encrypted channels, or leveraging legitimate business tools for unauthorized sharing.
Clearly, a new approach is needed—one that moves beyond static detection and provides real-time, dynamic protection.
What is Data Detection and Response (DDR) CyberSecurity?
Data Detection and Response (DDR) is a next-generation approach to data security, much like how Endpoint Detection and Response (EDR) transformed endpoint protection.

DDR provides real-time monitoring, behavioral analysis, and full lifecycle tracking to detect, analyze, and prevent data breaches before they happen.
(Learn more about CyberServal's DDR: How DDR Works)
- Traditional DLP = Rule-based scanning at static checkpoints.
- DDR = Continuous monitoring from data creation to transmission.
DDR isn’t just an enhancement to DLP—it’s a fundamental shift in how data security is handled.
What problems does DDR solve that DLP can’t?
👉 Download our latest DDR whitepaper to explore how to prevent costly data breaches. The following are key problems DDR solves that DLP misses:
- End-to-End Data Tracking
Unlike DLP, which only scans data at fixed points, DDR, next-gen DLP solution monitors data continuously from creation to destination, eliminating blind spots and stopping:
- Encrypted Evasion – Detects sensitive data before encryption.
- Hidden Transfers – Identifies data concealed in archives or altered formats.
- Fragmentation Tactics – Flags extracted data being reassembled elsewhere.
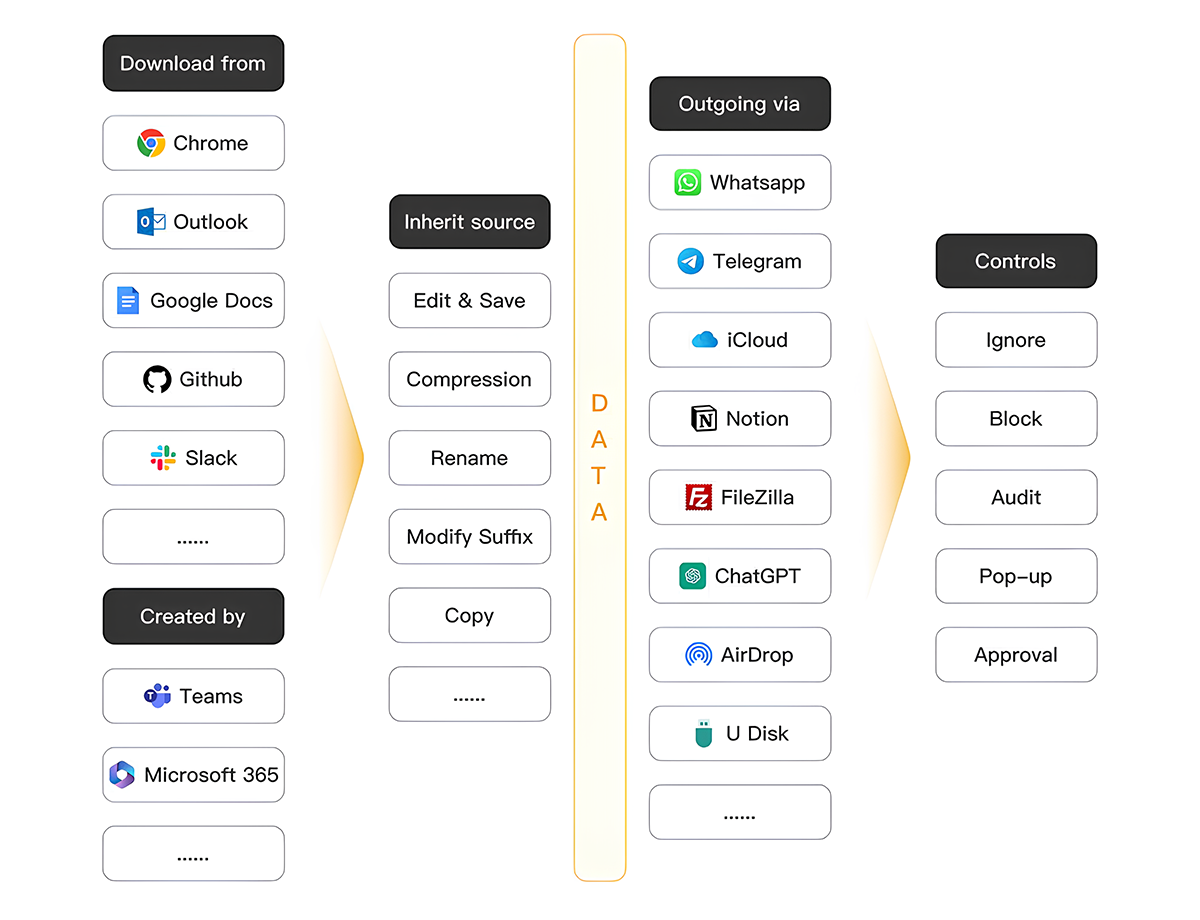
- Smarter, Context-Aware Protection
DLP relies on static rules; DDR understands behavior. Instead of just scanning for keywords, DDR tracks a file’s origin, modifications, and movement, catching threats that traditional DLP misses—like sensitive data hidden in images or non-standard formats.
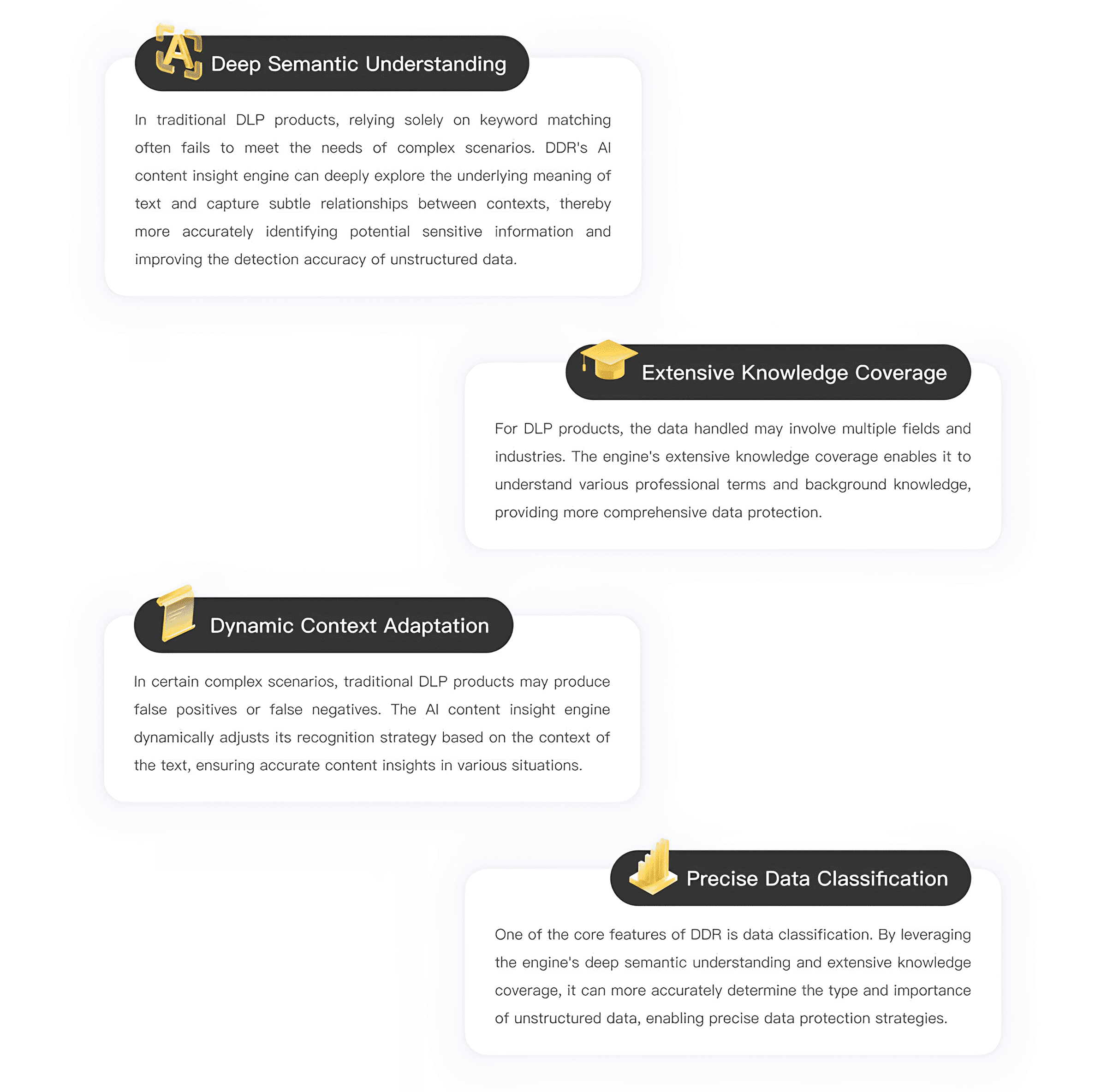
(Learn more about CyberServal's DDR: Super DLP: How DDR × DeepSeek AI is Redefining Data Protection)
- Stronger Defense Against Insider Threats
Insiders know how to bypass DLP. DDR stops:
- Unauthorized Transfers – Catching data sent to personal storage.
- Obfuscation Attempts – Detecting renamed, encoded, or encrypted files.
- Suspicious Behavior – Flagging unusual access patterns in real time.
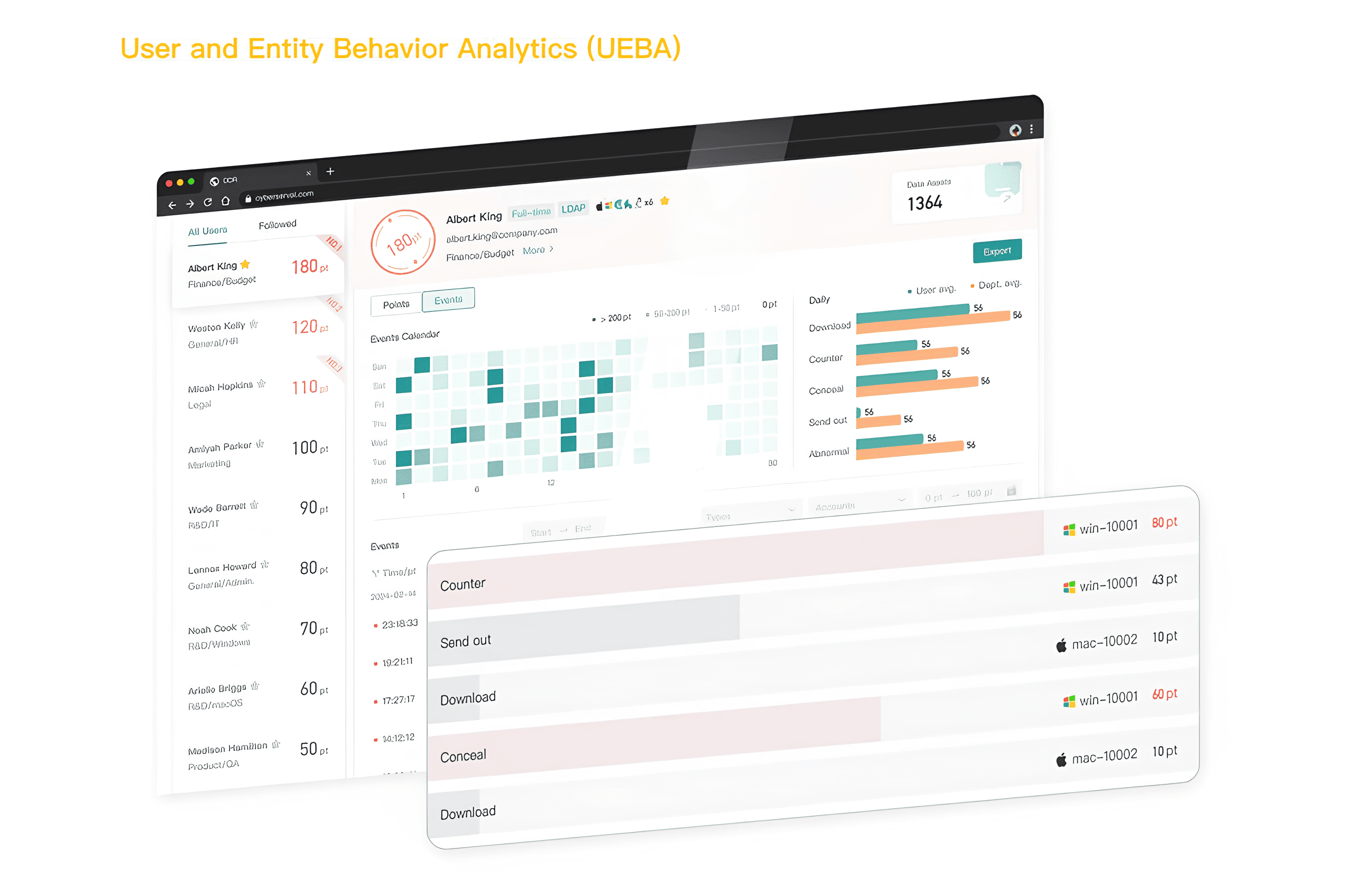
With continuous monitoring and real-time analysis, DDR sees what DLP can’t—stopping breaches before they happen.
How DDR detect insider threats
Detecting insider threats requires a multifaceted approach, incorporating both traditional and next-gen technologies. With the integration of LLMs (Large Language Models) and data lineage tracking, CyberServal’s Insider Risk Management platform provides a cutting-edge solution for detecting insider threats.
How DDR respond to detected threats
1. Implement Least Privilege Access
2. Monitor User Activities
3. Conduct Regular Employee Training
4. Implement Strong Authentication Mechanisms
5. Establish a Clear Data Governance Policy
6. Use Advanced Threat Detection Tools
👉Related Article: Insider Threats Protection with CyberServal Insider Risk Management
Why CyberServal?
CyberServal data security company offers a next-gen DDR solution that equips organizations with real-time, dynamic data protection. Our solution tracks data throughout its entire lifecycle, from creation to transmission, and provides advanced behavioral analysis to detect and mitigate threats before they happen. With continuous monitoring, proactive risk assessment, and real-time response capabilities, CyberServal’s DDR is the future of data security.
Contact us for a demo to stop data breaches before they happen.
