 Why Is Screen Capture the Hardest Problem for Traditional DLP?
Why Is Screen Capture the Hardest Problem for Traditional DLP?  What Happens When Security Disrupts Productivity?
What Happens When Security Disrupts Productivity?  What Does Next-Gen DLP Actually Need?
What Does Next-Gen DLP Actually Need?  How Do Invisible Watermarks Enable “Unseen” Protection?
How Do Invisible Watermarks Enable “Unseen” Protection?  Who Benefits from Multi-Dimensional Watermarking?
Who Benefits from Multi-Dimensional Watermarking?  When a Risk Happens, How Is Evidence Preserved?
When a Risk Happens, How Is Evidence Preserved?  Where Does Data Protection Go Next?
Where Does Data Protection Go Next?

Next-Gen DLP with Invisible Watermarks and Screen Capture
A confidential strategy deck. A closed internal meeting.
No files shared, no downloads logged, no emails sent. Yet weeks later, the same content appears where it should never be.
No alerts. No evidence. No clear suspect. For many organizations, this is how data leakage really happens today—not through sophisticated cyberattacks, but through something far more ordinary: a smartphone quietly pointed at a screen.
This is where traditional Data Loss Prevention (DLP) reaches its limits—and where next-gen DLP powered by Invisible Watermarks and Screen Capture forensics begins.
Why Is Screen Capture the Hardest Problem for Traditional DLP?
The digital-physical gap in data protection
Traditional DLP was built for a digital world. It monitors files, networks, endpoints, and applications. But screen capture—screenshots, screen recording, or mobile phone photography—happens outside the digital pipeline.
Key challenges:
- Screen photos never pass through file transfer channels
- Screenshot tools leave minimal forensic traces
- Mobile phone photography bypasses endpoint controls entirely
As a result, once sensitive data is displayed on a screen, it often becomes effectively untraceable.
Successful User Cases from CyberServal:
What Happens When Security Disrupts Productivity?
To address traceability, many organizations rely on visible watermarks—usernames, emails, or IDs stamped across documents.
But this approach creates new problems:
- Distracts employees during daily work
- Degrades readability of designs, code, and financial models
- Can be cropped, blurred, or avoided entirely
Executives and IT leaders face a familiar trade-off: Stronger security often means worse user experience.
And in modern, fast-moving organizations, poor experience leads to shadow IT, resistance, or security bypasses.
What Does Next-Gen DLP Actually Need?
Modern enterprises need a fundamentally different approach—one that aligns security with how people actually work.
- Protect data without interrupting employees
- Enable cross-media traceability, even after screen capture
- Provide credible forensic evidence, not assumptions
- Close the gap between digital and physical leakage
This is where CyberServal DDR (Next-Gen DLP) introduces a decisive shift.
How Do Invisible Watermarks Enable “Unseen” Protection?
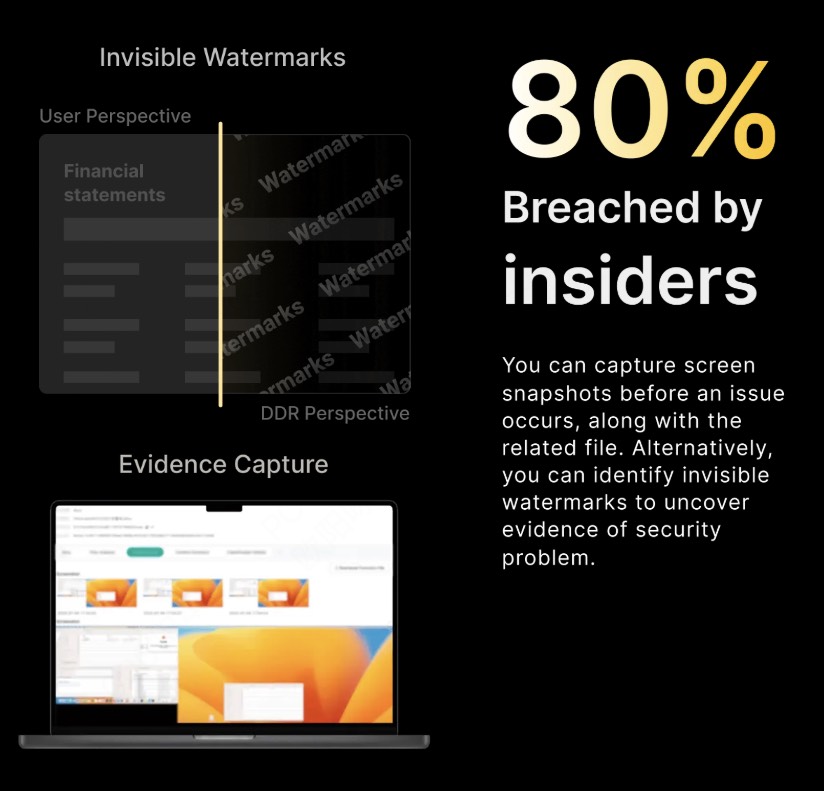
Invisible watermarks: protection without friction
Invisible watermarks embed identifiers into documents, images, or video content using advanced image-processing algorithms. They are:
- Completely invisible to the human eye
- Persistent across screenshots, recordings, and photography
- Resistant to compression, resizing, and re-sharing
Employees see a clean document. Attackers see nothing. Security teams see traceability.
I-SIFT: designed for real-world distortion
DDR uses an advanced I-SIFT (Intensity-based Scale-Invariant Feature Transform) algorithm. This allows watermark recovery even when content is degraded by:
- Camera lens distortion
- Lighting changes and reflections
- More patterns from screens
- IM app compression or format conversion
The result: robust attribution, even after physical-world capture.
Who Benefits from Multi-Dimensional Watermarking?
DDR supports multiple watermarking strategies to match different business scenarios:
- Invisible watermarks for daily internal work
- Visible or pixelated watermarks for external sharing
- QR codes for quick attribution
- Print and application-level watermarks for controlled environments
This flexibility allows organizations to balance risk, usability, and compliance—instead of enforcing blunt, universal controls.
When a Risk Happens, How Is Evidence Preserved?
From detection to defensible forensics
When a high-risk event occurs, DDR doesn’t just raise an alert—it captures context.
Automated evidence collection includes:
- Screenshots before, during, and after the event
- Reconstruction of up to 10 seconds of pre- and post-incident video
- Timestamped, tamper-resistant evidence chains
This transforms incident response:
- From guessing → to knowing
- From suspicion → to proof
- From fragmented logs → to a complete narrative
For legal, compliance, and executive teams, this matters just as much as prevention.
Download our technical whitepaper for an in-depth look at the underlying technologies behind CyberServal DDR.
Where Does Data Protection Go Next?
Invisible watermarks extend data protection beyond the screen.
They ensure that:
- Sensitive information remains accountable after display
- Physical-world leakage is no longer invisible
- “I took a photo” is no longer an escape route
In effect, DDR moves DLP into a new dimension—where data remains protected wherever it goes.
The future of data loss prevention is not louder warnings or heavier restrictions.
With Invisible Watermarks and Screen Capture forensics, next-generation DLP delivers:
- No disruption to employees
- No blind spots for security teams
- No ambiguity for leadership
CyberServal DDR proves a simple truth:
When security is invisible but accountability is absolute, data protection finally works.
If your organization is ready to close the last mile of data leakage, it’s time to rethink what DLP can—and should—do.
Click here to schedule a personalized live demo of CyberServal DDR and speak with one of our data security experts. Take the first step toward a smarter, quieter, and more effective data loss prevention posture.