 What is Red Team Blue Team Cyber Security Exercise?
What is Red Team Blue Team Cyber Security Exercise? When Do Companies Need Red and Blue Team Cyber Security?
When Do Companies Need Red and Blue Team Cyber Security? How Red Team Blue Team Cyber Security Exercise Will Help Companies
How Red Team Blue Team Cyber Security Exercise Will Help Companies How Often Should a Company Conduct an Exercise?
How Often Should a Company Conduct an Exercise? How to Verify If an Exercise Was Effective?
How to Verify If an Exercise Was Effective? DLP and Red Team Blue Team Exercise
DLP and Red Team Blue Team Exercise Why Choose CyberServal to Enhance Data Security?
Why Choose CyberServal to Enhance Data Security?
Red Team Blue Team Exercises for Real Cyber Security Situations
What is Red Team Blue Team Cyber Security Exercise?
The primary goal of CyberServal Red Team Blue Team cyber security exercise is to really test an companie's security capabilities from both an attacking and defending point of view. It's a lively, full - scale simulation that's meant to show the weak spots in people, processes, and technology, not just find the technical problems.
| Red Team | Blue Team |
|---|---|
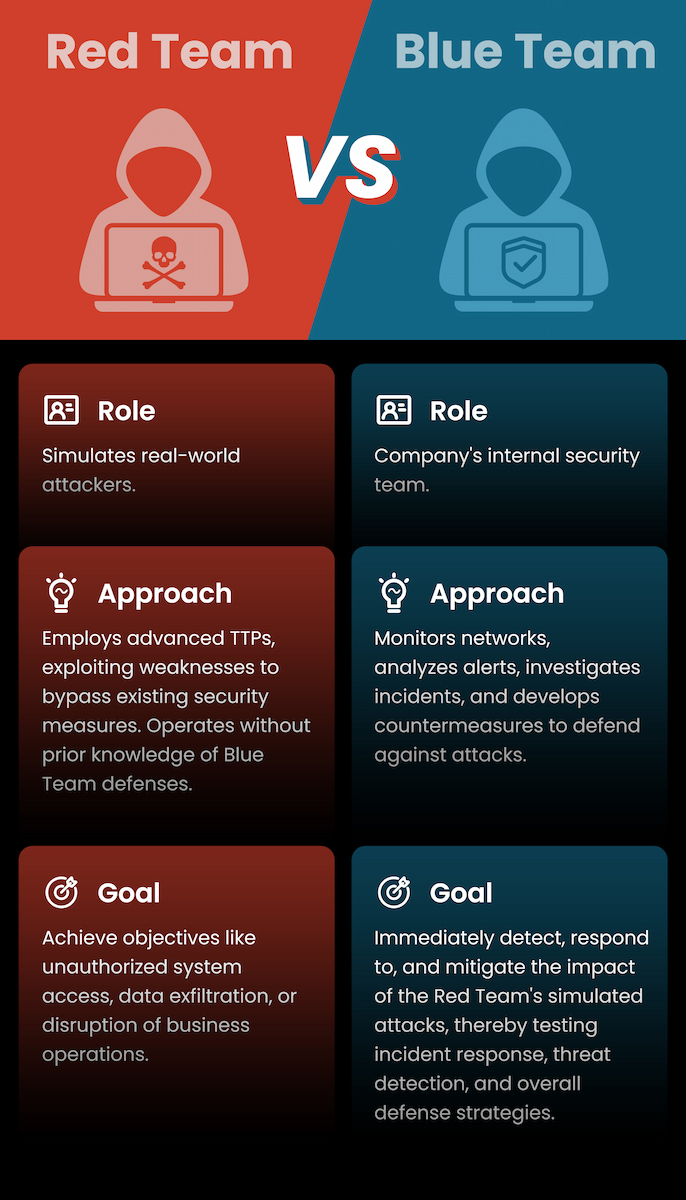
| Role: Simulates real-world attackers. Approach: Employs advanced TTPs, exploiting weaknesses to bypass existing security measures. Operates without prior knowledge of Blue Team defenses. Goal: Achieve objectives like unauthorized system access, data exfiltration, or disruption of business operations. | Role: Company's internal security team. Approach: Monitors networks, analyzes alerts, investigates incidents, and develops countermeasures to defend against attacks. Goal: Immediately detect, respond to, and mitigate the impact of the Red Team's simulated attacks, thereby testing incident response, threat detection, and overall defense strategies. |
It's not about one team beating the other. It's so the company can fully understand how strong its security really is, find the important holes, and make its overall security better, especially when it comes to protecting its most important thing: data.
When Do Companies Need Red and Blue Team Cyber Security?
While all companies can benefit from Red Team Blue Team exercises, certain situations and stages of growth make them particularly crucial:
- After Significant Security Investments: Following substantial investments in new security technologies (like advanced DLP solutions), a Red Team exercise can validate their effectiveness in a real-world scenario.
- Post-Breach or Near Miss: Companies that have recently experienced a data breach or a serious security incident often use these exercises to understand how the breach occurred, test new preventative measures, and rebuild confidence in their defenses.
- Compliance and Regulatory Requirements: Industries with strict compliance mandates (e.g., GDPR, HIPAA, PCI DSS) may find these exercises invaluable for demonstrating due diligence and validating security controls.
- Mergers and Acquisitions: Before or after integrating new systems and networks, an exercise can identify potential vulnerabilities introduced by the merger.
- Testing Incident Response Plans: Beyond tabletop exercises, a Red Team Blue Team engagement provides a live fire drill for an companie's incident response team.
- Maturity of Security Operations: Companies with a relatively mature security operations center (SOC) can leverage these exercises to refine their advanced detection and response capabilities. For less mature companies, it can highlight foundational weaknesses that need immediate attention.
- Protection of High-Value Assets: Companies handling extremely sensitive data (e.g., financial data, intellectual property, customer PII) or critical infrastructure should regularly conduct these exercises.
How Red Team Blue Team Cyber Security Exercise Will Help Companies
CyberServal red team and blue team exercises provide a multitude of benefits, especially for companies focused on data protection:
Attacking and Exploration
The Red Team initiates their attack, mimicking real adversaries. They use advanced tactics to exploit vulnerabilities, aiming to gain unauthorized access and explore the network. This stage provides a realistic assessment of security controls, including data loss prevention (DLP) systems, by actively trying to bypass them and exfiltrate sensitive data. It helps identify blind spots and gaps that might be missed by automated scans.
Command and Control
As the Red Team establishes a foothold, they set up command and control (C2) channels to maintain persistence and further their objectives. During this time, the Blue Team is actively engaged in improving detection and response capabilities. They leverage their detection and response (DDR) solutions to spot the sophisticated threats, triage alerts, and work to contain the Red Team's activities under pressure.
Attacking and Prevention
The exercise continues with the Red Team escalating their efforts to achieve their goals, while the Blue Team focuses on attacking and prevention. This is where incident response plans are validated under stress, revealing their practicality and completeness. The Blue Team actively implements countermeasures to prevent the Red Team from succeeding, fostering enhanced communication and collaboration across various security and IT teams as they work together to defend the environment.
Reviewing and Reporting
After the simulated attack concludes, a comprehensive reviewing and reporting phase takes place. The findings quantify risk and prioritize remediation by providing concrete evidence of exploitable weaknesses. This allows the company to focus on the most impactful vulnerabilities. The exercise also boosts security awareness among employees, who gain a better understanding of security protocols through exposure to the simulated social engineering tactics.
How Often Should a Company Conduct an Exercise?
The frequency of Red Team Blue Team exercises depends on several factors, including the companie's risk profile, industry, regulatory requirements, the maturity of its security program, and budget. However, a general guideline is:
- Annually or Bi-Annually for Most: For many companies, conducting a full Red Team Blue Team exercise annually or every two years is a good starting point. This allows time for remediation efforts to be implemented and for new threats and technologies to emerge.
- After Major Changes: If there are significant changes to the IT infrastructure, mergers/acquisitions, or deployment of major new systems, an exercise should be considered sooner
- Continuous Improvement Cycle: For highly mature companies in high-risk sectors, a more continuous red teaming approach might be beneficial, with smaller, more focused exercises conducted more frequently throughout the year.
The key is to integrate these exercises into a broader security continuous improvement cycle, ensuring that lessons learned are translated into tangible security enhancements. Contact us now for a free trial, sales@cyberserval.com
How to Verify If an Exercise Was Effective?
An effective Red Team Blue Team exercise yields actionable insights, not just a list of vulnerabilities. Here are key indicators of effectiveness:
- Comprehensive Reporting: A detailed report outlining the Red Team's methodologies, attack paths, exploited vulnerabilities, and the Blue Team's detection and response efficacy.
- Identified Gaps and Weaknesses: The exercise should clearly highlight previously unknown or underestimated weaknesses in security controls, processes, or personnel.
- Actionable Recommendations: The report should provide specific, prioritized recommendations for remediation, improvement of security tools, policy adjustments, and training needs.
- Improved Blue Team Performance: Did the Blue Team improve their detection rates, response times, and overall coordination during the exercise? Post-exercise debriefs and performance metrics are crucial.
- Validation of Existing Controls: The exercise should confirm the effectiveness of well-configured and properly implemented security controls, including DLP solutions, giving confidence in existing investments.
- Enhanced Security Posture: Ultimately, the measure of effectiveness is whether the exercise leads to a tangible and measurable improvement in the company's overall security posture and resilience against real-world threats.
- Post-Exercise Remediation: The true test of effectiveness lies in the company's commitment to implementing the recommendations and verifying their impact.
DLP and Red Team Blue Team Exercise
The relationship between Data Loss Prevention (DLP) and Red Team Blue Team exercises is mutually beneficial and very important. For a DLP Solutions company like ours, this connection is essential for showing the real - world value of our products.
DLP as a Key Defensive Layer: During an exercise, DLP solutions are really tested. The Red Team will try hard to steal sensitive data, like customer records, intellectual property, financial documents, or internal communications, using different methods. This directly checks if the DLP policies we've put in place can detect, stop, or give an alert about these attempts through different channels (email, cloud storage, USB, network shares).
Validating DLP Effectiveness: The exercise gives real - world proof of how well DLP solutions stop unauthorized data from leaving. It can show if the policies are too lenient, too strict (causing false alarms), or if there are areas that the current settings don't cover. For example, if the Red Team can steal data through a channel we're not watching, it shows a big problem with our DLP.
Improving DLP Policies and Rules: The information we get from a Red Team exercise is really useful for making DLP policies better. If the Red Team can get around a DLP control, it shows us how to make that rule stronger, add new rules, or cover more data types or ways data can leave.
Training for DLP Analysts: Blue Team members who manage and respond to DLP alerts get hands - on experience in telling normal traffic from malicious attempts to steal data. This helps them handle incidents faster and more effectively.
Demonstrating ROI for DLP: For companies that spend a lot on DLP, these exercises clearly show that they're getting their money's worth by showing how the solution can stop data breaches when under attack. This is a strong argument for stakeholders and executives.
Proactive Threat Intelligence: The tactics, techniques, and procedures (TTPs) the Red Team uses to get around DLP controls give us useful information about threats. We can use this to improve our DLP strategies and stay ahead of new threats.
In short, a Red Team Blue Team exercise is like a real - world test for DLP solutions. It makes sure they're not just theoretical protections but practical, strong barriers against data loss.
Why Choose CyberServal to Enhance Data Security?
At CyberServal, we know that strong data security is not a choice but a must. Our advanced DLP solutions are made to be the key part of your defense plan, giving the best protection against the loss of sensitive data. But even the most advanced technology needs to be checked and improved all the time.
By adding CyberServal Red Team Blue Team exercises to your current security measures, you can go from just having theoretical protection to having real - world resilience. When these exercises are done precisely and analyzed by experts, they are the best test for solutions like CyberServal DLP, showing how well they can stop complex data stealing attempts. They let companies find weaknesses in advance, make their incident response better, and finally, protect their most valuable things. Work with CyberServal. Not only can you use the top - level DLP in the industry, but you can also check its effectiveness through strict, real - world simulations. This way, your data will stay safe, no matter what threats come.